The role of Identity Access Management in enabling co-creation in the scaleup world
The fastest growing tech scaleups base their product development on collaborative co-creation with customers and external business partners. To support this way of working without exposing the company for unintended risk it is important to have a structured approach to managing external users.

Jul 01, 2024
Kantega SSO has the pleasure to work with many exciting customers in around 60 countries around the world. One of the customer groups that we are especially excited to work with are fast-growing technology companies with international ambitions. We are based in the Nordics, a region representing only 3% of global software demand but according to a recent McKinsey report the fastest growing software funding hub in Europe. (The export surge for Nordic software companies | McKinsey).
Because our domestic markets are relatively small, it is a necessity for Nordic software companies to plan for international expansion already from the very start. This is probably one of the reasons that our region is home to tech unicorns like Klarna, Spotify and Zendesk.
Fast growth in the technology industry almost always implies a way of working that involves daily collaboration across ecosystems including customers, vendors and partners. Many tech scaleups have chosen Jira and Confluence as their preferred platforms for partnership collaboration. This means that thousands of external users, ie. users coming from a different domain than that of the company that owns the Atlassian instance, need access to the software for innovation projects to operate efficiently. In our experience external users make up 5-10% of the total user base in a typical company but they often take a disproportional amount of the IT administrator’s attention. The reason for this is both that the turnover of external users tends to be higher than for internal employees and that relatively few companies have structured processes for provisioning and off-boarding of external users.
In some companies external users are created on an ad-hoc basis, often because a business stakeholder puts pressure on the IT administrator to open up access for a high-profile project, but then forgotten since there have been few tools available to help keep track of them and to enable the administrator to act proactively when they no longer are in use. Other companies decide not to open for external users at all because they do not have the manual resources to establish a sound administration of them, which is sub-optimal for the business, and both might slow down and block important innovation projects.
In Kantega SSO we believe that opening up for external users is an important enabler for innovation in technology-based scaleups and that it is important to put robust processes in place to ensure sound administration of this user group. In our experience there are some key things to consider and plan for to make external sharing run smoothly both for the business and IT.
Consider whether there is a need for full access of if read-only access is enough.
We sometimes meet companies that have chosen to give full access to their Confluence, although all they need is a read-only access to internal documentation that the company does not want to share in the public domain. For this use case we recommend to put SSO-protected read only access in place, so that your company has full control over the authentication and is able to monitor the external users’ activity so that your IT department can respond quickly to changes in behaviour and rapidly close down access that no longer are active to reduce unnecessary risk exposure: SSO-verified Anonymous Access - Kantega SSO Enterprise - Confluence (atlassian.net)Make sure to have tools in place that allow you to monitor login activity.
In our experience, around 20% of an average company’s digital accounts belong to people who have left the company, changed roles or for other reasons no longer have a legitimate reason for needing the access. For external users this percentage seem to be higher, since many companies do not have a structured approach to administrating this user group. This represents a risk that it is important to think through. What happens if the external consultant who was in the company for a 6 month long project moves on to working for one of your competitors and nobody closes down his/her access to your systems?
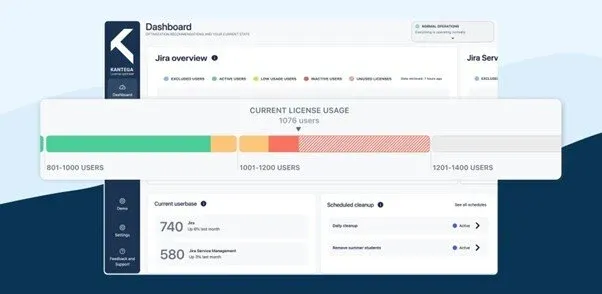
In Kantega SSO we have built four apps, for Jira and Confluence supporting both cloud and data centre host products, that allow you as an IT administrator to scan your user base for activity. This means that you instantly get visual overviews of the activity levels for both internal and external users so that you can start asking questions to department managers or project owners responsible for users external to your company.
3. Make sure to set up automatic off-boarding rules to close accesses when the legitimate reason no longer is valid.
Large companies often have a centralised IDP where all internal user accounts are managed and structured processes in place, for example managed by HR or another support function to ensure that digital accesses are deactivated when employees leave or change departments. High growth companies do not always have resources to scale up support functions and the pace of growth makes it challenging for IT to keep up with the changes across the organisation. The IT department is often stretched between a variety of tasks and the process of offboarding external consultants or beta testers who have been allowed access to Jira or Confluences is down-prioritised and handled on an ad-hoc basis.
With a tool that enables the IT administrator to configure rule-based offboarding rules you can reduce the risk of accesses being kept open without legitimate reason and that those accounts can be taken advantage of by someone with malicious intent.
Every company is different and has their specific needs. Examples of typical offboarding rules within the enthusiastic group of tech scaleups that have co-created the functionality in Kantega SSOs User Cleanup apps with us are to deactivate accounts that have been inactive for 30 days, to deactivate external consultants’ accounts at 23:00 on the last day of the project they were hired for or to give pilot customers that are let in to the company’s software to give feedback on product prototypes a time-limited access that expires after 60 days.
All of these rules are easily configurable for customers who use one of Kantega’s Automated User Cleanup & Deactivator apps that are available for trial on: Automated User Cleanup & Deactivation for Jira | Atlassian Marketplace
Our team has experience supporting tech scaleups from all continents in setting up sound administration of external users and in systemizing automatic offboarding rules. If you are looking for advice, feel free to book a meeting with us on Select a meeting · Book a support or demo meeting with Kantega SSO (youcanbook.me).