The role of Identity Access Management in achieving DORA Compliance
The deadline for European financial institutions to ensure DORA compliance is approaching. Identity Access Management plays an important role in DORA.

Jun 15, 2024
On January 17th 2025, time runs out to ensure DORA compliance for the approximately 22 000 companies across the European Union and the European Economic Area that belong to the financial sector in Europe. The financial sector has been through a rapid digitalisation over the past 20-25 years and as a result its digital infrastructure has become vital for society’s ability to operate. A hostile attack on national payments infrastructure could for example block the flow of liquidity across society, which rapidly would put many companies out of business and result in workers not being paid salaries to provide for their families. The objective of DORA is to protect the financial sector in Europe and to make sure that it stays resilient in the event of severe operational digital disruption.
To comply with DORA, financial institutions and their subcontractors need complete visibility into how and where human and machine users access protected data. Article 9 of the regulation clearly states that all regulated entities are responsible for putting processes in place to ensure that only users with a legitimate reason have access to corporate assets and that the company has procedures to ensure sound administration of those access rights.
In Kantega SSO we have more than 10 years of experience supporting the financial sector in protecting their digital assets. In our experience, the following identity access management mechanisms are key for a CIO to have in place to achieve the level of protection that EU mandates in the DORA regulation.
- Efficient provisioning procedures: The fewer provisioning points for user accesses, the less vulnerable your company is to intrusion. Combining a centralised IDP like Entra ID or Okta with SSO on all software applications is the best way to achieve this. An SSO application like Kantega Single Sign On blocks all other entries to the local software (for example Jira or Confluence) and can be configured to enforce enhanced security like multifactor authentication from the central IDP.
- Comprehensive audit logs: A key requirement in DORA is to be able to trace exactly what users that were impacted by a data breach. To be in a position to provide this information it is key that your identity management application logs all login attempts, both successful and unsuccessful and that it is easy for your IT administrator to extract these logs in a format that non-technical colleagues can understand.
- Configuration backup: Software upgrades sometimes lead to unexpected outcomes. In the interest of quickly being able to restore access if something goes wrong, it is helpful to make sure that your software provider automatically takes configuration backups ahead of each upgrade. Ideally the provider should also provide your company with the option to trigger backups so that your company can schedule them in a way that suits your business logic. In Kantega SSO we have many customers who have expressed this need and we have solved it by offering our customers to trigger configuration backups via a REST API.
Backup & restore (Snapshots of config) - Kantega SSO Enterprise - Confluence (atlassian.net)
- Configurable automatic offboarding: Article 9 in DORA states very clearly that only users with a legitimate reason should have access to protected data owned by a financial institution. This applies both to company employees (internal users) and to the growing population of external users employed by vendors, customers or business partners that need access to internal systems for collaboration projects to work efficiently. In order to stay compliant without risking slowing down important business activities, the CIO should make sure to have tools in place that allow the company to scan the user database for activity and to configure rules that automatically close down accesses that no longer are needed. Typical rules based on experience from Kantega’s customer base are that all users are deactivated after 30 days of inactivity or that consultants hired for a specific project get their access deactivated automatically at 23:00 on the last day of the project.
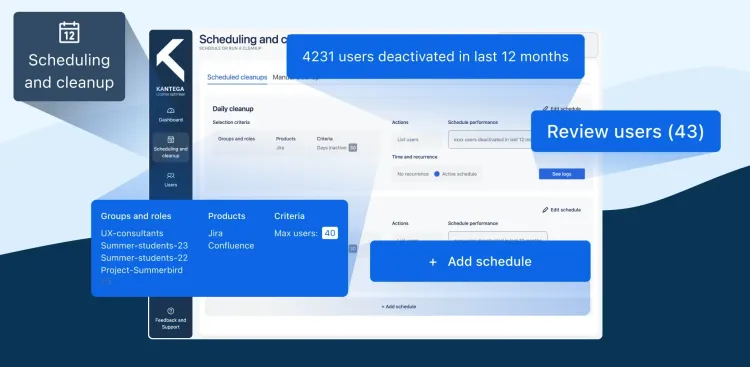
All Kantega’s Single Sign On plugins support single schedule user cleanup configuration. For customers with more advanced needs, we have developed a separate app called Automated User Cleanup and Deactivation that is available both for Jira and Confluence on Data Center and Cloud.
Automated User Cleanup & Deactivation for Jira | Atlassian Marketplace
- Protected read-only access for external users: In our experience, external users like consultants, customers or vendors make up 5-10% of the total user base for an average company but often require at least 50% of the IT administrator’s attention. In some cases these users only need read-only access, for example to technical documentation that is published on the company’s intranet but that the organisation does not want to share in the public domain. Instead of giving these users full access, we in Kantega SSO recommend to enable SSO-protected read-only access that enables your company to authenticate these users before allowing them to access your documentation.
SSO-verified Anonymous Access - Kantega SSO Enterprise - Confluence (atlassian.net)
- Automatic off-boarding rules for external users: In our experience the lack of formal processes for dealing with external users exposes many companies to risks that can not be tolerated when under DORA regulation. The best way to avoid keeping accesses open for externals that no longer have a legitimate need for the access is to install a software that allows you to scan user accounts with external domains for activity and to configure automatic offboarding rules. In our experience tools that quickly give the IT administrator an intuitive graphical visualisation of activity levels are more efficient in keeping on top of the important process of protecting internal assets.
In essence, no approach to protecting you company’s digital assets is stronger than the strength of the identity access management systems that guards its borders. This means that a well thought-through approach to provisioning, login, audit logging, backups and offboarding of user accounts is key to ensuring compliance with the Digital Operations Resiliency Act.
For more information about DORA and what it means for you: Digital Operational Resilience Act (DORA) (europa.eu)
For more information about Kantega SSO and how we can help, feel free to book a meeting with us: Select a meeting · Book a support or demo meeting with Kantega SSO (youcanbook.me)
